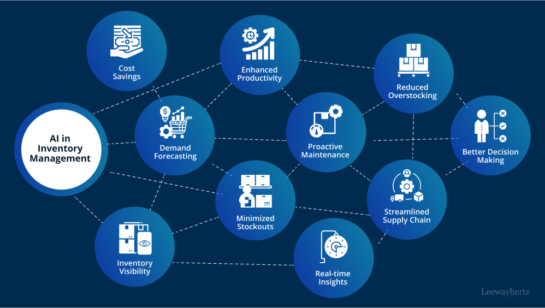
How Artificial Intelligence Can Help Organizations With Inventory Management: Boost Efficiency and Accuracy Artificial intelligence (AI) is transforming the way organizations manage their inventory. AI […]

4 Ways Artificial Intelligence Can Strengthen Business Security: Enhancing Protection and Efficiency In today’s digital age, businesses face growing cybersecurity threats. Protecting sensitive data and […]
5 Ways AI Technology Can Help Small Business Succeed Artificial Intelligence (AI) is not just for big corporations anymore; it’s also becoming a powerful tool […]

3 Digital Indicators Of An Inside Threat: Essential Warning Signs for Cybersecurity In cybersecurity, insider threats pose a significant risk to organizations. These threats often come […]

Urgent Warning: Cybercriminals Exploiting Trust in Reputable Organizations In today’s digital landscape, cyber threats are becoming increasingly sophisticated, targeting businesses and personal computer users. One […]

The Top 10 Reasons Law Firms Must Outsource Their IT Support to a Local Managed IT Provider: Maximizing Efficiency and Security Outsourcing IT support to […]

Is Your MSP Helping Or Hindering Your Information Systems Investments? Evaluating the Impact Investing in information systems is crucial for any business aiming to stay […]

Why Leading Organizations Must Continue To Invest In Information Systems Infrastructure In The Second Half Of 2024: Key Benefits and Strategic Advantages Investing in information […]

How To Permanently Delete Data From Your Computer: A Comprehensive Guide Deleting data from your computer is crucial to protect your sensitive information. Whether you […]